Common Email Scams: Access Restricted

Access Restricted/ Credential Farming
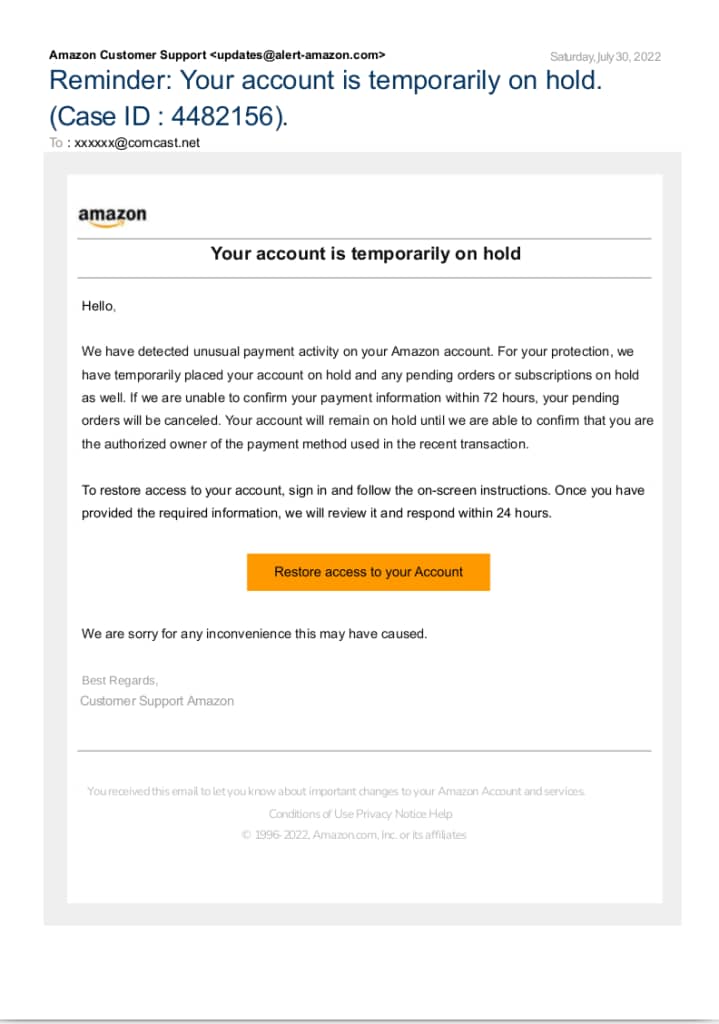
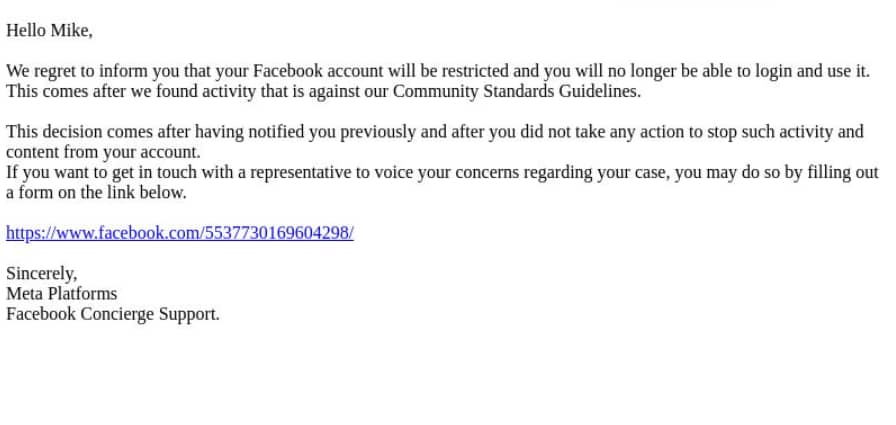
Access Restricted email spams are spoofing attacks. The sender pretends to be from a legitimate company like banks, organizations, financial institutions, or service providers like Facebook, Google, Amazon, Microsoft, etc. In the email, there will be a threat that said service is closing your account temporarily. Sometimes, there will be an attachment instead of a simple plain-text email, but the content will remain the same.
The email’s content is often a notification that your account has been locked and you need to sign in using the link or button in the same email. Their goal is to get you to log into their website, which looks like the original service provider page. From here they will save your credentials, which they can use to perform any number of malicious activities.
Access Disabled Email Scam Example
Signs to Look Out For
- Misspelled email addresses or different email addresses on the header. See email spoofing explained here.
- Sudden notification of unauthorized online purchases, updated online account passwords, unauthorized access to your computer, etc.
- Generic greetings like “Dear user”, “Dear @youremail.com”, and “Dear valued customer”. Spam messages are usually sent in bulk, so spammers may not have time to add individual names. But don’t be too confident, some elaborate email scams can gather names and use them to personalize these scams.
- Suspicious links. Hover your cursor over the link or button on the email to check if the link leads to a legitimate website. Be careful to avoid accidentally clicking on any links while checking.
How to Avoid This Email Scam
Be skeptical. It’s good practice to visit the website directly rather than clicking any links or buttons on emails. Fraudulent emails are designed to look exactly like the official emails of the companies they are trying to impersonate, so many people fall for them. Here are other tips to avoid becoming a victim of this email scam:
- Contact the business using the official phone number or email address listed on their official website if you want to verify the email’s authenticity.
- Never send sensitive information through e-mail, especially if you’re not sure of the sender’s identity.
- Check your online accounts directly from the website for notifications about access restrictions.
- Install anti-spam and anti-spyware on your personal or work computer.
- Report or delete suspected phishing emails to prevent other people from falling victim to the same email scams.